Cloud Foundation: 29 Capabilities across 6 Categories¶
Cloud Foundations templates (scripts, templates, policies, etc.) serve as a helpful reference for building your own Landing Zone solution
What is Cloud Foundations¶
Cloud Foundations (CF) is an initiative that offers a guided path to assist customers to deploy, operate, and govern (DOG) their workloads in the cloud. By leveraging AWS Solution Guidance across a wide range of AWS Services, AWS Solutions, and Partner Solutions, Cloud Foundations (CF) empowers customers to make informed decisions and navigate the complexities of establishing a production-ready environment with ease. Whether you're just starting your cloud journey or looking to validate the operational maturity of your existing environment, Cloud Foundations provides assurance that your infrastructure is primed and ready to handle all your production workloads.
IaC Templates¶
The Cloud Foundations on AWS template library provides infrastructure as code templates, policies, scripts, and other resources that can accelerate establishing your Cloud Foundation on AWS. The repository is organized by the following topics:
1. Control Tower¶
The Control Tower directory contains various templates, scripts, and infrastructure as code for assisting in setting up and managing your
control towerenvironment.
2. Identity Management¶
The identity directory is a collection of templates, examples and solutions to be referenced in creating and managing your cloud foundation environment relevant to
identity management.
3. Logging¶
The logging directory is a collection of templates, examples and solutions to be referenced in creating and managing your cloud foundation environment relevant to
centralized logging.
4. Tagging¶
The tagging directory is a collection of templates, examples and solutions to be referenced in creating and managing your cloud foundation environment relevant to implementing
tagging.
5. Template Management¶
The template management directory is a collection of templates, examples and solutions to be referenced in creating and managing your cloud foundation environment relevant to setting up and sharing various templates in your cloud environment.
1. Governance, Risk Management, and Compliance¶
* AWS CloudTrail: `aws-tf-cloudtrail-log`
* AWS Resource Naming Convention: <organisation>-<env>-<stack>-<operation>-<AWS-resource-type>
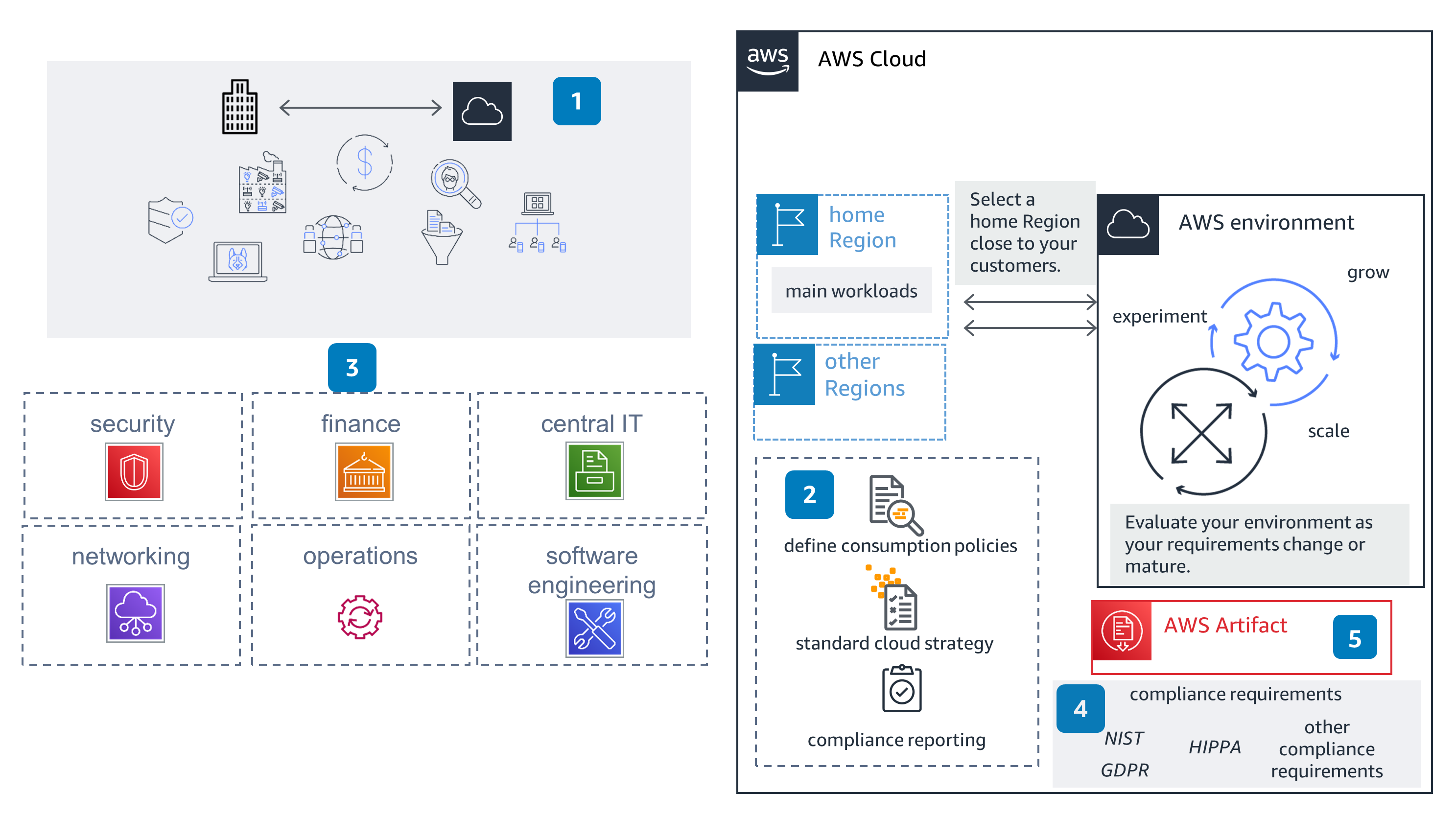
Guidance for Governance on AWS
- 1. Establish a relationship with your cloud provider, understanding what services are available in what region, and the different requirements they fulfill.
- 2. Define your cloud consumption policies and strategy. What services will be available in the cloud? How will your workloads and applications be deployed on the cloud?
- 3. Build knowledge about the cloud and the different technologies it provides across your organization. Identify key stakeholders that will be involved when you establish the different capabilities of your AWS environment. Build cloud capability and enable your stakeholders across your organization
- 4. Identify what compliance frameworks you need to adhere your workloads on the cloud to, and learn about the shared responsibility model. Ensure your data and your workloads provide you with enough information to report your compliance requirements.
- 5. Use AWS Artifact to collect the AWS security and compliance reports and select online agreements. Reports available in AWS Artifact include service organization control (SOC) reports, payment card industry (PCI) reports, and certifications from accreditation bodies across geographies and compliance verticals that validate the implementation and operating effectiveness of AWS security controls.
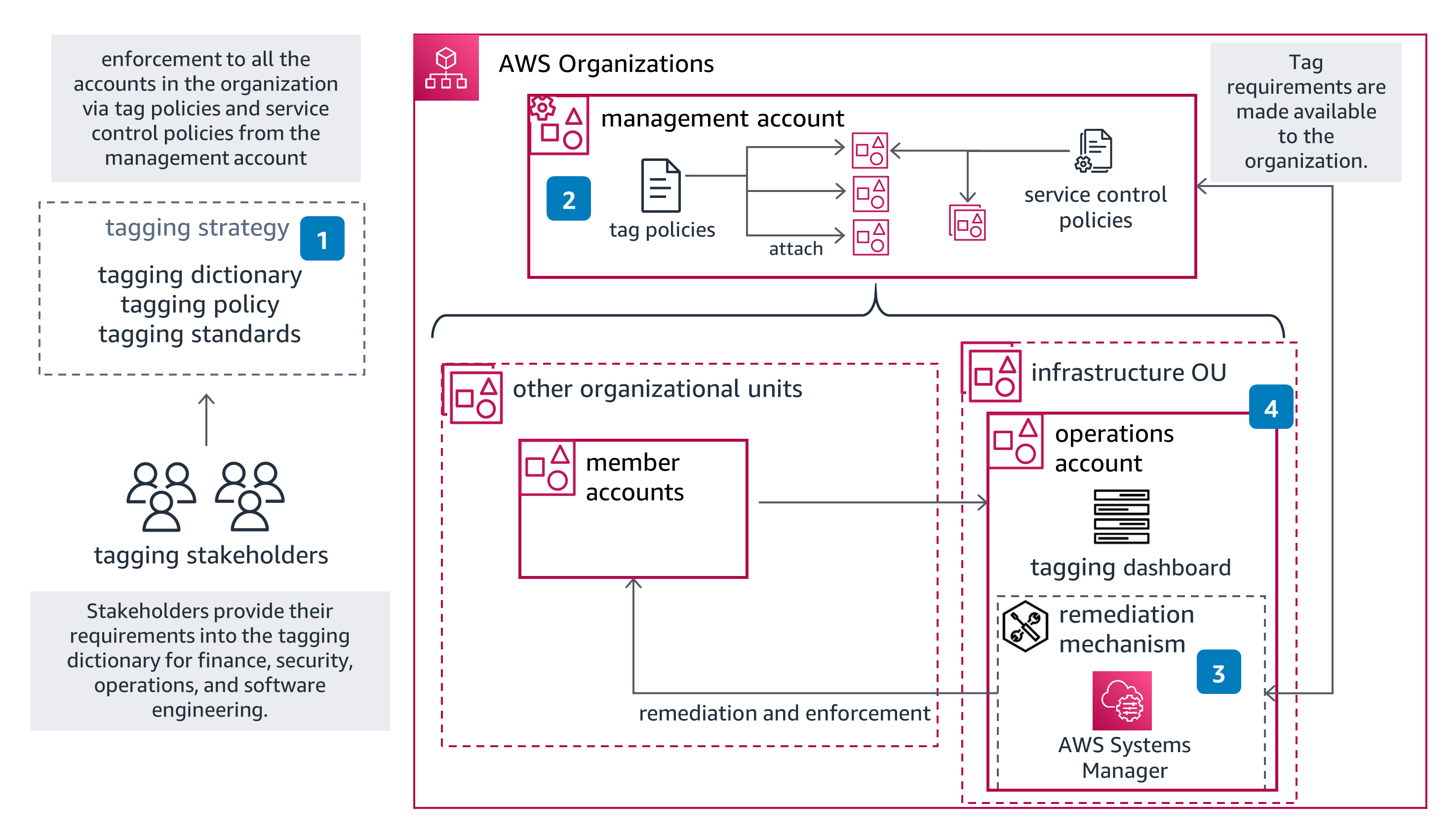
Guidance for Tagging on AWS
- 1. Define a tagging strategy: decide what the mandatory tags are, your tagging policy, and your tagging standards. Stakeholders across the company provide the information required to the Cloud team to standardize tagging.
- 2. Create tag policies in AWS Organizations and attach them to the relevant organizational units (OUs) and accounts to generate resource compliance reports and understand how resources are tagged in your environment.
- 3. AWS Systems Manager can help you tag resources through automations across your AWS environment. You can also use resource groups to bulk tag your resources across your environment.
- 4. Within your operations account, create a dashboard that can display the metadata assigned to your resources and act as a remediation mechanism.
2. Security¶
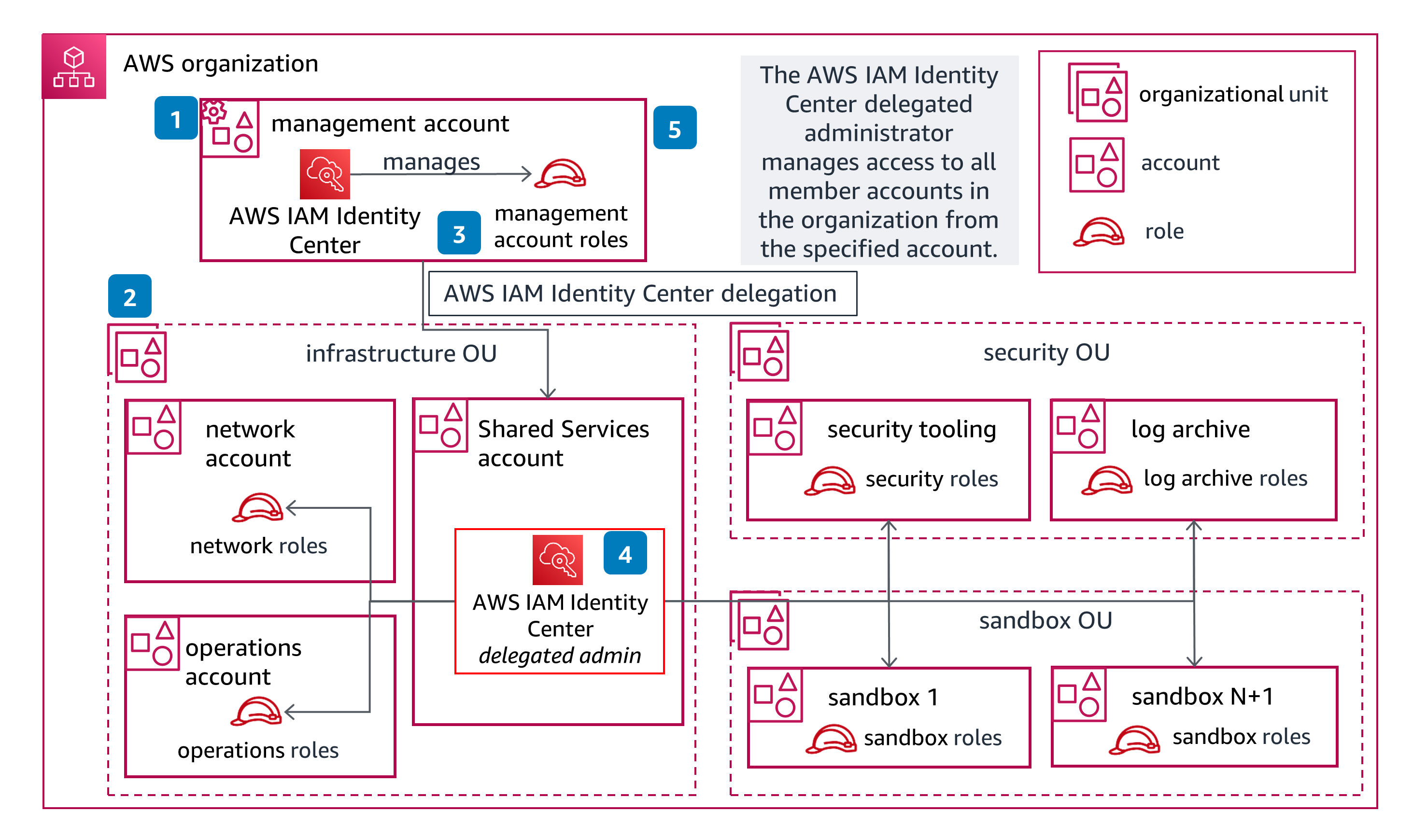
Guidance for Identity Management & Access Control on AWS
- 1. On your management account, create an AWS IAM Identity Center instance and set up your organization.
- 2. Create the initial set of recommended accounts to configure your foundation. Follow the recommendations included in the Production Starter Organization.
- 3. Connect to your external IdP, such as Okta, or create the Users and Groups within AWS IAM Identity Center to organize access across your environment. Create permission sets for access to your management account and assign them to the management account users.
- 4. Delegate AWS IAM Identity Center to your Shared Services account, log in with the AWS IAM Identity Center role, create permission sets, and assign them to the groups and users for the member accounts in your AWS organization.
- 5. Using your AWS IAM Identity Center role to administer the management account, create Preventive Controls using Service Control Policies in the management account, and delegate the security, network, and operation services to their corresponding AWS accounts in your environment.
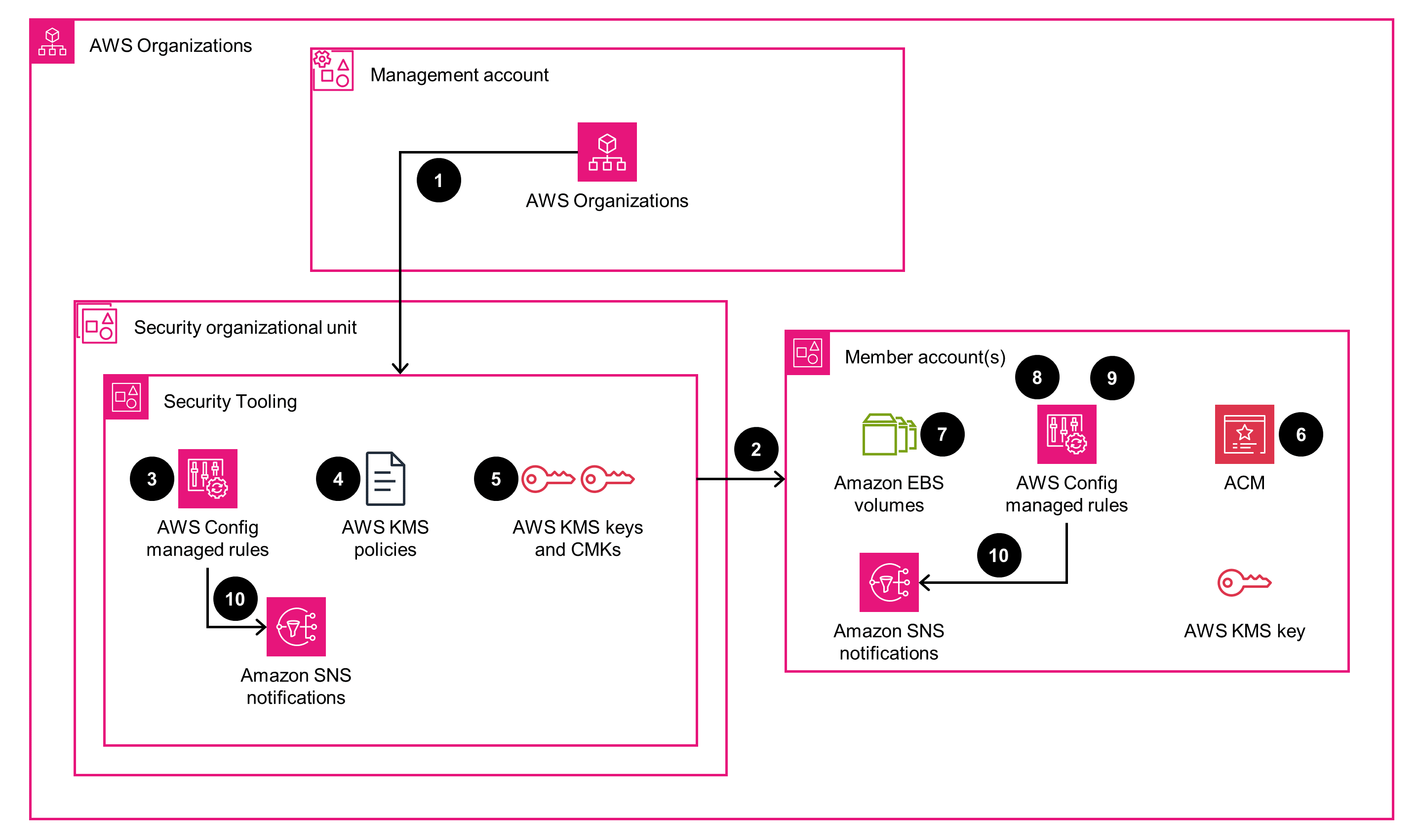
Guidance for Encryption & Key Management on AWS
- 1. Deploy and configure an AWS Security Tooling account for central key storage operations and sharing with AWS Organizations.
- 2. Enable AWS Key Management Service (AWS KMS) automatic key rotation for AWS KMS key lifecycle management.
- 3. Deploy an AWS Config managed rule to monitor AWS KMS lifecycle management in the Security Tooling account.
- 4. Configure AWS KMS key policies to allow secure access across Organizations.
- 5. Use AWS-managed AWS KMS keys and customer managed keys (CMKs) as required by your governance requirements.
- 6. Use AWS Certificate Manager (ACM) to automate the generation and management of SSL certificates.
- 7. Enforce Amazon Elastic Block Store (Amazon EBS) volume default behavior to be encrypted on generation. Monitor the encryption using AWS Config managed rules on all Organizations member accounts.
- 8. Deploy AWS Config managed rules to monitor the encryption of AWS services with network connections.
- 9. Deploy AWS Config managed rules to monitor the encryption of AWS services with persistent data.
- 10. Receive notifications for compliance using Amazon Simple Notification Service (Amazon SNS).
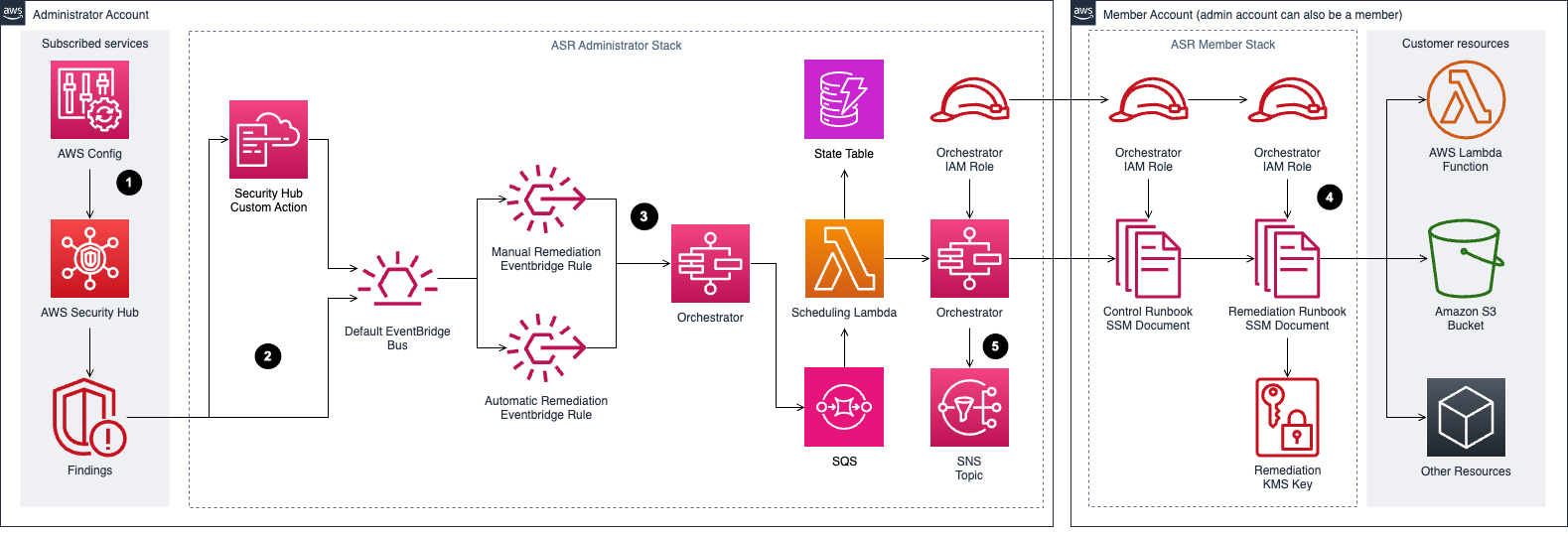
Automated Security Response on AWS
- Prerequisite: Security Hub findings aggregated in the delegated administrator account initiate AWS Step Functions. Step Functions invokes a remediation SSM automation document in the member account containing the resource that produced the AWS Security Hub finding.
- Automated Security Response on AWS
3. Infrastructure¶
TBD
3.1. Network Connectivity Capability
The Network Connectivity capability enables you to create, manage, and monitor secure, scalable, and highly available networks for your applications and workloads. This includes connectivity within the cloud, Hybrid connectivity, IP address management, network logging and monitoring, and DNS management.
- Building a Scalable and Secure Multi-VPC AWS Network Infrastructure
-
CF11.S1 Scenario: Connectivity within the Cloud Environment
-
CF11.S2 Scenario: IP Address Management | Network Designing and Planning
- Design IP Address Scheme: CIDRs & IP Utilization
-
CF11.S3 Scenario: Network Orchestration - Centralized and/or Distributed Network Configuration and Management
-
CF11.S4 Scenario: Hybrid Connectivity - Hybrid Environment Setup
-
VPN
-
BGP
-
CF11.S5 Scenario: Network Logging and Monitoring Setup
-
CF11.S6 Scenario: DNS Management - Construct DNS Setup for Applications
Terraform IaC¶
- S3 bucket:
aws-terraform-org-state-us-east-1>tf-org-aws>management
Network Connectivity > Implementation Priorities¶
AWS Network Connectivity Management Tools¶
Network Connectivity – AWS Implementation Guidance¶
- Network account
- Access to the network account for networking administrators
- Cloud WAN for centralized management – AWS Transit gateway for advanced complex routing scenarios
- AWS Resource Access Manager to share attachments across the organization
- IPAM service to ensure not overlapping of IP addresses
- Specific runbooks including step-by-step guidance to operate repeatable tasks
4. Resilience & Business Continuity¶
TBD
5. Centralized Operations¶
TBD
6. Finance¶
* ☑️ The `CloudHealth` billing platform on the admin (billing) account.
* ☑️ S3 bucket: `management-cost-usage-report`
Guidance for Resource Inventory Management on AWS
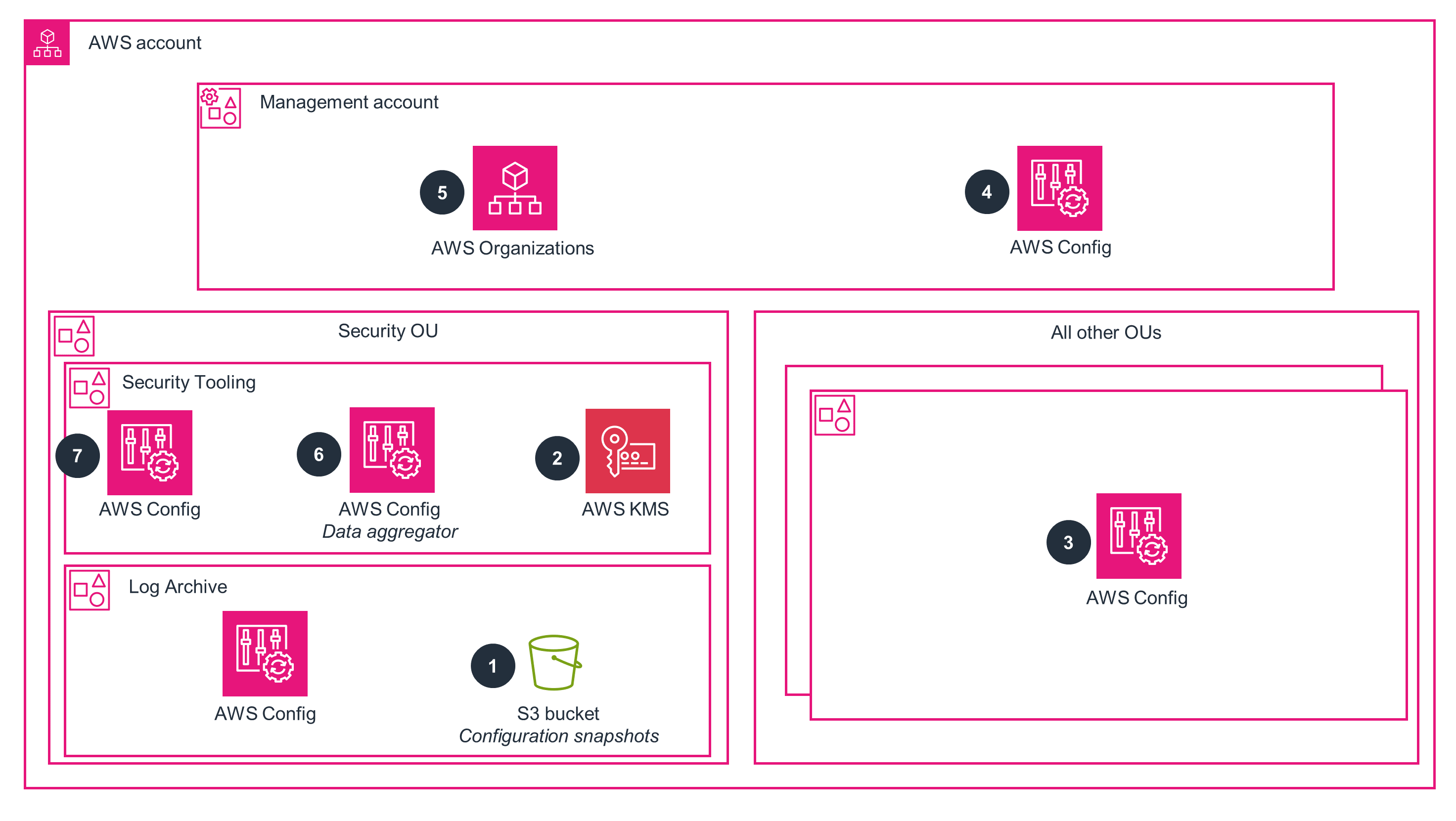
- 1. Create an Amazon Simple Storage Service (Amazon S3) bucket that will hold the AWS resource configuration snapshots and history.
- 2. Optionally, create an AWS Key Management Service (AWS KMS) key in the Security Tooling organizational unit (OU) account. This account will be used to encrypt configuration history and snapshot files using server-side encryption with AWS KMS customer-managed keys (CMKs). If you do not use an AWS KMS key, the AWS Config data will be encrypted at rest using AES-256 encryption.
- 3. Deploy an AWS Config configuration recorder and delivery channel to all operating Regions (Regions that you are not prohibited with service control policies [SCPs]) in all member accounts. Configure the
delivery channelto send resource configuration information to the S3 bucket in the Log Archive account for audit and retention purposes. - 4. Deploy AWS Config
configuration recorderanddelivery channelto all available Regions in the Management account. Configure the delivery channel to send management account resource configuration information to the S3 bucket in the Log Archive account. - 5. Delegate AWS Config administration to the
Security Tooling OUaccount to allow for AWS Config administration outside of the management account. - 6. Deploy an AWS Config
multi-Account, multi-Region data aggregatorin the Security Tooling OU account to aggregate account and Region data for the organization. This will provide visibility to organization resources and AWS Configconfiguration compliance. - 7. Deploy
AWS Config Rulesto organization accounts to evaluate resource compliance. You can deploy rules with organization AWS Config rules, with conformance packs, or by using automation, such as AWS CloudFormation StackSets.
Cloud Financial Management Solutions
References
- 📚 Solutions for Cloud Foundations
- AWS Cloud Readiness Assessment (Cloud Adoption Framework)
- Establishing Your Cloud Foundation on AWS - Whitepaper
-
Cloud Foundations on AWS Solutions Library
Use AWS Cloud Foundation Solutions: Visit the Cloud Foundation Solutions in the AWS Solutions Library for vetted solutions and guidance on Cloud Foundations.
-
Cloud Foundations in the AWS Architecture Center
Continually optimize your foundation: Visit Cloud Foundations in the AWS Architecture Center for additional guidance to continue to implement and optimize your capabilities.
-
Cloud Foundations Accelerator Well-Architected Custom Lens
Setup the Cloud Foundations Accelerator Well-architected Custom Lens to track progress and calibrate your foundational environment.
-
Cloud Foundations Acceleration Day Workshop
Complete the Cloud Foundations Acceleration Day workshop to establish or verify the essential elements of your cloud foundation are in place.
-
AWS Multi-Account Security Governance Workshop
This workshop is designed to help you get familiar with a common pattern for centralized security governance across a multi-account AWS deployment. You will be working with AWS Organizations to establish security guardrails (preventive and detective) and enable centrally managed security services for detection/logging/visibility.