Building a Scalable AWS Global Network Infrastructure Across Hybrid Environments: A Case Study¶
AWS Transit Gateway can revolutionize your organization's network
AWS Transit Gateway is a game-changing solution designed to simplify and elevate your organization's network architecture, especially in scenarios involving intricate setups of multiple AWS accounts and Amazon Virtual Private Clouds (VPCs).
-
Effortless VPC-to-VPC Connectivity Scaling: AWS
Transit Gatewayseamlessly connects VPCs within the same AWS Region and across AWS Regions, ensuring uninterrupted communication among your workloads. -
Bridging AWS Regions and Spoke Networks: Whether you’re utilizing AWS
Site-to-Site VPN, AWSDirect Connect, orTransit Gateway Connect, this solution provides the flexibility to link AWS resources across different regions and hybrid networks. -
Multicast Support: Certain industries, like financial services and media and entertainment, demand multicast support, which AWS
Transit Gatewayreadily accommodates. -
Secure Access via AWS
PrivateLink: Forge secure connections to applications in other VPCs using AWS PrivateLink, ensuring all network traffic remains within the AWS backbone, eliminating the need for anInternet Gateway (IGW). -
Hybrid Connectivity to Data-Centers:
AWS Transit Gatewaycaters to two common hybrid connectivity approaches, depending on your organization’s objectives. -
AWS
Direct Connectand AWSSite-to-Site VPN: AWS offers two robust methods for hybrid network connections.
Overview¶
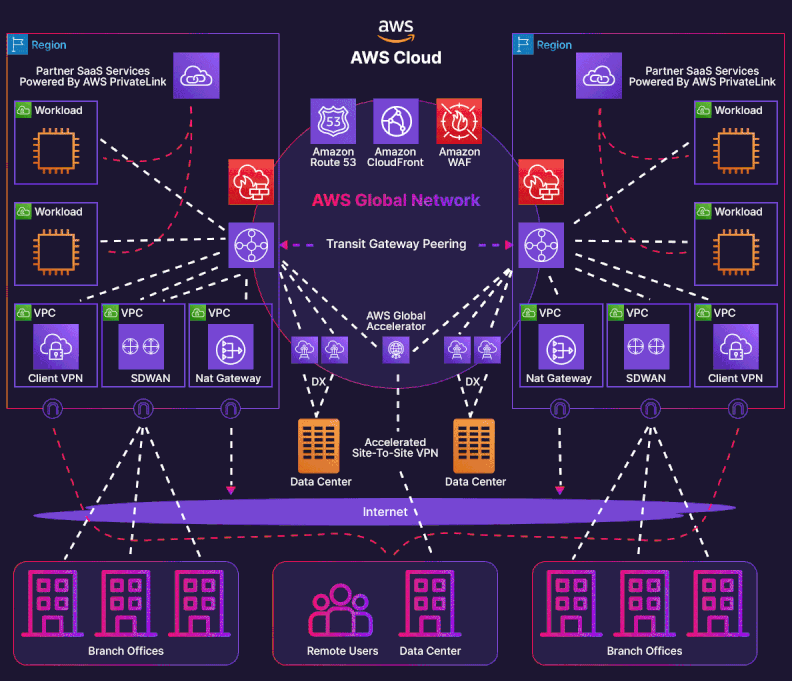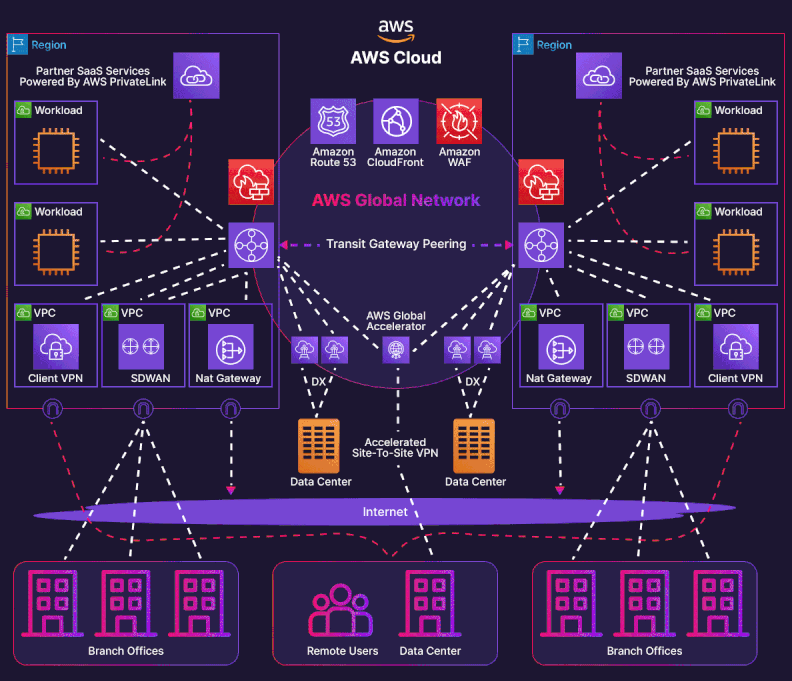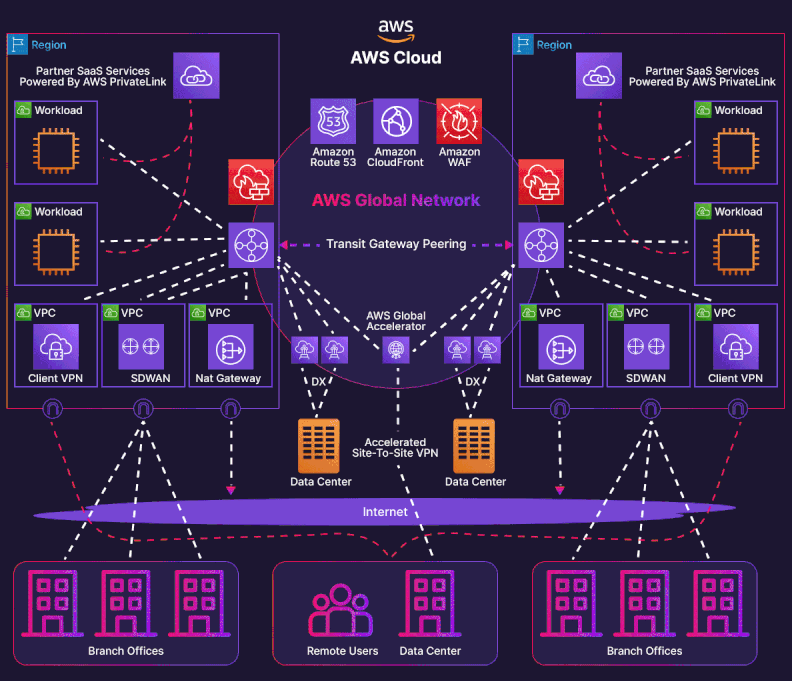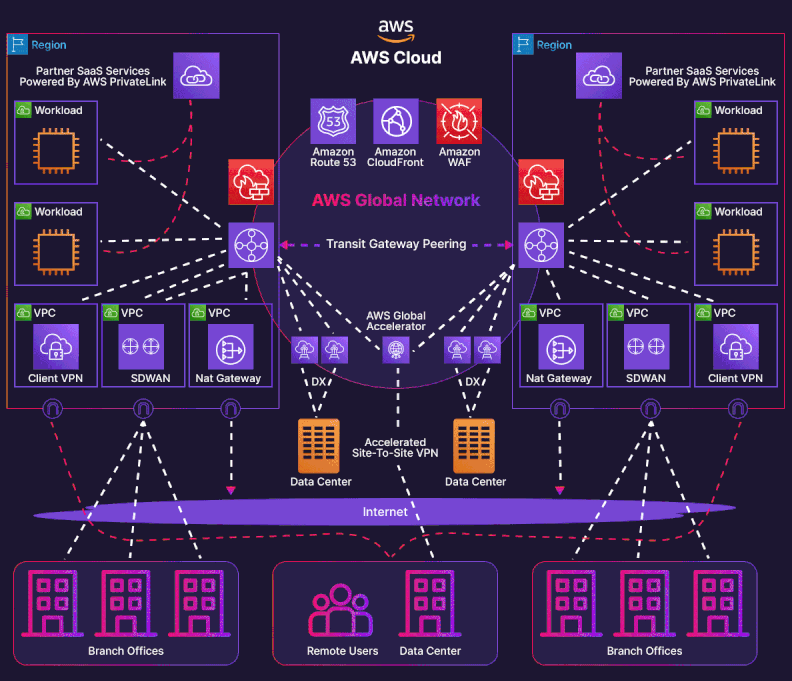
Enterprises leveraging AWS across multiple geographic locations often encounter complexity when integrating their hybrid-cloud architectures. This case study delve into an advanced, multi-account AWS landing zone that spans on-premises data centers in Auckland (NZ) and Sydney (Australia), three AWS Direct Connect (DX) connections, and two Transit Gateway (TGW) domains—tgw-aws-shared-services and tgw-aws-outbound-security; incorporating Megaport and Equinix as partners. The architecture supports a shared-services account and an outbound-security account, strategically designed for security, performance, and cost optimization.
The goals are to:
- Provide deterministic, low-latency transport for “east–west” hybrid traffic.
- Enforce security zoning between shared services and egress / inspection domains.
- Enable rapid, prefix-based route governance across autonomous teams.
Network Architecture¶
Physical and Logical Layout¶
The as-built design features three Direct Connect (DX) connections:
- dxcon-aws-dx-NZ-AUS: Auckland Data-Center 1 Gbps, jumbo frames enabled, no MACsec, encryption explicitly disabled.
- dxcon-aws-equinix: Equinix 1 Gbps at Equinix SY1–SY4, jumbo frames enabled, no MACsec, encryption down.
- dxcon-megaport: Megaport 200 Mbps at Global Switch SY6, VLAN 1905, jumbo frames enabled, no MACsec, encryption down.
| DX Connections | Location & Provider | Capacity | Encryption Mode | VLAN | Jumbo Frame | MACsec Capable |
|---|---|---|---|---|---|---|
| dxcon-aws-dx-NZ-AUS | DCDH6 Auckland Data-Center (NZ) | 1 Gbps | no_encrypt (Encryption Down) |
100 | ✔︎ | ✘ |
| dxcon-aws-equinix | EqSY3 Equinix SY1–SY4 (AUS) |
1 Gbps | unknown (Encryption Down) |
101 | ✔︎ | ✘ |
| dxcon-megaport | GbSY6 Megaport MCR → Global Switch SY6 (AUS) |
200 Mbps | unknown (Encryption Down) |
1905 | ✔︎ | ✘ |
Connectivity Insights
- VLAN Segmentation: Maintained clearly (1905 Megaport, 100 Auckland, 101 Equinix) ensuring isolation.
- Transit Gateway (TGW): Managed by AWS ASN 64600, providing a scalable, highly available hub-and-spoke model.
- MACsec: Currently not enabled, posing a risk for data confidentiality over direct physical lines.
Logical Topology¶
- AS 64600 advertises customer prefixes through public VIFs that land on the two TGWs.
- Jumbo frames (MTU = 8500) are enabled end-to-end to maximise payload efficiency.
- All VIFs are Transit-type, handing off to TGWs rather than individual VPCs.
flowchart TD
%% ───────────────────────────────
%% 🏢 ON-PREM DATA-CENTRES
%% ───────────────────────────────
subgraph "Customer Premises"
direction TB
AUC[Auckland DC: NZ]
SYD[Sydney DC: AUS]
end
%% ───────────────────────────────
%% ⛓️ DIRECT CONNECT connectionS
%% ───────────────────────────────
%% Each connection is modelled as an intermediate node so
%% we can attach BFD or per-link metrics later.
dxcon-aws-dx-NZ-AUS[dxcon-3<br/>1 Gbps<br/>Auckland ↔ AWS]
dxcon-megaport[dxcon-1<br/>200 Mbps<br/>Megaport SY6]
dxcon-aws-equinix[dxcon-2<br/>1 Gbps<br/>Equinix SY1]
AUC -- "connection" --> dxcon-aws-dx-NZ-AUS
SYD -- "connection" --> dxcon-megaport
SYD -- "connection" --> dxcon-aws-equinix
%% ───────────────────────────────
%% 🗄️ DIRECT CONNECT GATEWAY (single hop)
%% ───────────────────────────────
dcgw[tgw-megaport-dx-gateway]
dxcon-aws-dx-NZ-AUS --> dcgw
dxcon-megaport --> dcgw
dxcon-aws-equinix --> dcgw
%% ───────────────────────────────
%% 🔀 TRANSIT GATEWAY (logically central)
%% ───────────────────────────────
tgw[tgw-aws-shared-services: ASN 64600]
dcgw ==> tgwAuckland DC ─┐ ┌─ dxcon-megaport ─ Megaport SY6 ─┐
│ │ │
├─ dxcon-aws-dx-NZ-AUS (1 G) TGW: tgw-aws-shared-services
│ │ │
Sydney DC ──┘ └─ dxcon-aws-equinix ─ Equinix SY1 ──┘
Virtual Interfaces (VIFs) & Direct Connect Gateways¶
| VIF ID | Attachment | VLAN | Type | DX Gateway | Consuming TGW |
|---|---|---|---|---|---|
| dxvif-1 | dxcon-megaport |
1905 | Transit | tgw-megaport-dx-gateway |
tgw-aws-shared-services |
| dxvif-2 | dxcon-aws-equinix |
101 | Transit | tgw-aws-outbound-security-dx-gateway |
tgw-aws-outbound-security |
| dxvif-3 | dxcon-aws-dx-NZ-AUS |
100 | Transit | tgw-aws-shared-services-dx-gateway |
tgw-aws-shared-services |
==> WIP ...
| VIF ID | Name | Type | VLAN | DX Connection | TGW Attachment |
|---|---|---|---|---|---|
| dxvif-1 | megaport-aws-transit-vif | Transit | 1905 | dxcon-megaport | tgw-aws-shared-services |
| dxvif-2 | tgw-aws-shared-services-equinix | Transit | 101 | dxcon-aws-equinix | tgw-aws-shared-services |
| dxvif-3 | tgw-aws-shared-services-auckland | Transit | 100 | dxcon-aws-dx-NZ-AUS | tgw-aws-shared-services |
Direct Connect gateways decouple each VIF from a single Region, allowing multi-Region TGW attachments in future without re-provisioning ports.
Direct Connect Gateways facilitate sharing DX connections across accounts:
- Direct-Connect-gateway-1 (Megaport-MCR-to-AWS) manages prefixes for multiple shared CIDR ranges.
- Direct-Connect-gateway-2 (aws-shared-services) handles specific point-to-point (/32) routes.
- Direct-Connect-gateway-3 (aws-shared-services) controls extensive CIDR ranges across shared-services domains.
Transit Gateway Associations¶
TGW – tgw-aws-shared-services¶
- Route domain for corporate services, build pipelines, and identity systems.
- Accepted prefixes (summarised):
10.1.0.0/16,10.15.48.0/20 … 10.15.96.0/20,10.20.0.0/19 … 10.20.96.0/20,10.22.64.0/20 … 10.23.112.0/20,10.31.0.0/16,10.31.176.0/20.
TGW – tgw-aws-outbound-security¶
- Egress / inspection domain front-ending Zscaler / Firewall / IDS stacks.
- Advertises a superset of shared-services plus
/32inspection next hops:10.24.128.182/32,10.24.129.233/32,10.31.208.171/32,10.31.209.37/32.
Prefix Control Add/Remove prefixes in the Direct Connect Gateway association rather than the TGW route table—this cleanly separates network-core change (DXGW) from application-layer routing (TGW).
===
Transit Gateway Associations¶
Transit Gateways (tgw-aws-shared-services and tgw-aws-outbound-security) leverage BGP routing (ASN 64600) for robust inter-VPC and DX connectivity, explicitly controlling allowed prefixes for enhanced security segmentation. Traffic domains are well-defined:
- Shared Services account manages broad CIDR range distributions.
-
Outbound Security account enforces strict, smaller /32 CIDR routing for critical secure endpoints.¶
Security Considerations¶
| Gap | Risk | Mitigation |
|---|---|---|
| Encryption Down / no_encrypt | Traffic on provider layer-2 may be viewed or spoofed. | Enable MACsec on new ports (802.1AE) or overlay IPsec (VPN over DX) until carrier upgrades. |
| MACsec = false | Hardware not enabled; frames in the clear. | Request MACsec-capable cross-connects at SY6, SY1, Auckland. |
| Shared TGW ASN (64600) | Single ASN may complicate route-leak isolation. | Consider dedicated ASNs per TGW or per account, then neighbour-tag in TGW route-tables. |
| Jumbo Frame mismatch | Silent MTU drops break 4-way TCP handshake. | Verify mtu 8500 end-to-end using ping -s 8972 -M do. |
FinOps & Governance¶
- Tag every DXVIF & TGW with
CostCenter,Environment,BusinessUnit, andDataSensitivity. -
Port-hour charge optimisation:
-
Use Scheduled Auto-Start on the 200 Mbps Megaport to lower idle‐time costs.
- Aggregate low-volume DEV/TEST traffic via the 200 Mbps link; reserve 1 Gbps ports for PROD.
- Forecast DX Data-Out to on-prem via Cost Explorer > Usage Type = "USW2-DataTransfer-Out-Bytes" to pre-commit in SAVINGS PLANS for Data Transfer (preview).
As-Built Network Topology Diagram (Mermaid)¶
Version 3
flowchart TD
%% ───────────────────────────────
%% ⛓️ ON-PREM COLOCATION SITES
%% ───────────────────────────────
subgraph OnPrem ["On-Prem Colocations"]
direction TB
AUC[Auckland-DC<br/>dxcon-aws-dx-NZ-AUS: 1 Gbps, no_encrypt, VLAN 100]
SY6[Global Switch SY6<br/>dxcon-megaport: 200 Mbps, enc down, VLAN 1905]
SY1[Equinix SY1-SY4<br/>dxcon-aws-equinix: 1 Gbps, enc down, VLAN 101]
end
%% ───────────────────────────────
%% 🌐 VIRTUAL INTERFACES (Transit VIFs)
%% ───────────────────────────────
subgraph VIFs ["Transit VIFs"]
direction TB
dxvif3["dxvif-3<br/>VLAN 100"]
dxvif1["dxvif-1<br/>VLAN 1905"]
dxvif2["dxvif-2<br/>VLAN 101"]
end
AUC --- dxvif3
SY6 --- dxvif1
SY1 --- dxvif2
%% ───────────────────────────────
%% 🗄️ DIRECT CONNECT GATEWAYS
%% ───────────────────────────────
subgraph DCGWs ["Direct Connect Gateways"]
direction TB
dcgw1["tgw-megaport-dx-gateway"]
dcgw2["tgw-aws-outbound-security-dx-gateway"]
end
dxvif1 --> dcgw1
dxvif2 --> dcgw1
%% legacy: should be dcgw1 for shared-services
dxvif3 --> dcgw2
%% ───────────────────────────────
%% 🔀 TRANSIT GATEWAYS (ASN 64600)
%% ───────────────────────────────
subgraph TGWs ["Transit Gateways"]
direction LR
tgw_shared["tgw-aws-shared-services"]
tgw_out["tgw-aws-outbound-security"]
end
dcgw1 ==> tgw_shared
dcgw2 ==> tgw_out
%% ───────────────────────────────
%% 🗒️ PREFIX SUMMARY (truncated)
%% ───────────────────────────────
tgw_shared -.-> prefixes1["10.1.0.0/16 … 10.31.176.0/20"]
tgw_out -.-> prefixes2["10.24.128.182/32 … 10.31.209.37/32"]
%% ───────────────────────────────
%% ⚠️ BFD MONITORING (Corrected)
%% ───────────────────────────────
bfd[BFD Session]
bfd -. BFD Monitor .-> dxcon-megaport
Version 2
flowchart TD
%% ───────────────────────────────
%% ⛓️ PHYSICAL DX LOCATIONS
%% ───────────────────────────────
subgraph "On-Prem Colocations"
AUC[Auckland-DC<br/>1 Gbps]
SY6[Global Switch SY6<br/>200 Mbps]
SY1[Equinix SY1-SY4<br/>1 Gbps]
end
%% Direct Connect connection anchors
dxcon-aws-dx-NZ-AUS["dxcon-aws-dx-NZ-AUS<br/>aws-auckland<br/>no_encrypt"]
dxcon-megaport["dxcon-megaport<br/>Megaport SY6<br/>unknown_enc"]
dxcon-aws-equinix["dxcon-aws-equinix<br/>Equinix SY1<br/>unknown_enc"]
AUC --- dxcon-aws-dx-NZ-AUS
SY6 --- dxcon-megaport
SY1 --- dxcon-aws-equinix
%% ───────────────────────────────
%% 🌐 VIRTUAL INTERFACES
%% ───────────────────────────────
dxvif3["dxvif-3<br/>VLAN 100<br/>Transit"]
dxvif1["dxvif-1<br/>VLAN 1905<br/>Transit"]
dxvif2["dxvif-2<br/>VLAN 101<br/>Transit"]
dxcon-aws-dx-NZ-AUS -- "VLAN 100" --> dxvif3
dxcon-megaport -- "VLAN 1905" --> dxvif1
dxcon-aws-equinix -- "VLAN 101" --> dxvif2
%% ───────────────────────────────
%% 🗄️ DIRECT CONNECT GATEWAYS
%% ───────────────────────────────
dcgw1["tgw-megaport-dx-gateway"]
dcgw2["tgw-aws-outbound-security-dx-gateway"]
dxvif1 --> dcgw1
dxvif2 --> dcgw1
%% shared-services landing
dxvif3 --> dcgw1
%% ───────────────────────────────
%% 🔀 TRANSIT GATEWAYS (ASN 64600)
%% ───────────────────────────────
tgwShared["tgw-aws-shared-services<br/>ASN 64600"]
tgwOut["tgw-aws-outbound-security<br/>ASN 64600"]
dcgw1 ==> tgwShared
dcgw2 ==> tgwOut
%% Prefix summaries (truncated)
tgwShared -.- p1["10.1.0.0/16 …"]
tgwOut -.- p2["10.24.128.182/32 …"]
%% ───────────────────────────────
%% 📡 BFD MONITORING
%% ───────────────────────────────
subgraph "Monitoring"
style Monitoring fill:#ffffff00,stroke:#555,stroke-dasharray:5 5
bfd1["BFD dxcon-megaport"]
bfd2["BFD dxcon-aws-equinix"]
%% intentionally NOT linked
bfd3["BFD dxcon-aws-dx-NZ-AUS"]
end
bfd1 -. "udp/3784" .- dxcon-megaport
bfd2 -. "udp/3784" .- dxcon-aws-equinix
%% bfd3 link intentionally omitted to surface a resiliency gapVersion 1
flowchart TD
%% ───────────────────────────────
%% ⛓️ PHYSICAL DX LOCATIONS
%% ───────────────────────────────
subgraph "On-Prem Colocations"
AUC[Auckland-DC: 1 Gbps]
SY6[Global Switch SY6: 200 Mbps]
SY1[Equinix SY1-SY4: 1 Gbps]
end
%% Direct Connect connection anchors
dxcon-aws-dx-NZ-AUS["dxcon-aws-dx-NZ-AUS<br>aws-auckland<br>no_encrypt"]
dxcon-megaport["dxcon-megaport<br>Megaport SY6"]
dxcon-aws-equinix["dxcon-aws-equinix<br>Equinix SY1"]
AUC --- dxcon-aws-dx-NZ-AUS
SY6 --- dxcon-megaport
SY1 --- dxcon-aws-equinix
%% ───────────────────────────────
%% 🌐 VIRTUAL INTERFACES
%% ───────────────────────────────
dxvif-3["dxvif-3<br>VLAN 100<br>transit"]
dxvif-1["dxvif-1<br>VLAN 1905<br>transit"]
dxvif-2["dxvif-2<br>VLAN 101<br>transit"]
dxcon-aws-dx-NZ-AUS -- VLAN100 --> dxvif-3
dxcon-megaport -- VLAN1905 --> dxvif-1
dxcon-aws-equinix -- VLAN101 --> dxvif-2
%% ───────────────────────────────
%% 🗄️ DIRECT CONNECT GATEWAYS
%% ───────────────────────────────
dcgw-1["tgw-megaport-dx-gateway"]
dcgw-2["tgw-aws-outbound-security-dx-gateway"]
dxvif-1 --> dcgw-1
dxvif-2 --> dcgw-1
%% INTENTIONAL: should attach to dcgw-1 for SHARED-SERVICES
dxvif-3 --> dcgw-2
%% ───────────────────────────────
%% 🔀 TRANSIT GATEWAYS (ASN 64600)
%% ───────────────────────────────
tgw-shared["tgw-aws-shared-services"]
tgw-out["tgw-aws-outbound-security"]
dcgw-1 ==> tgw-shared
dcgw-2 ==> tgw-out
%% Prefix summaries (truncated for brevity)
tgw-shared -.-> prefixes1(("10.1.0.0/16 …"))
tgw-out -.-> prefixes2(("10.24.128.182/32 …"))
%% ───────────────────────────────
%% ⚠️ MISSING BFD MONITOR LINK (INTENTIONAL)
%% ───────────────────────────────
bfd[BFD-Session]
%% bfd -.x.- dxcon-megaport
DataSync Diagram¶
flowchart TD
%% ─────────────────────────
%% ON-PREMISES (REGION / POP)
%% ─────────────────────────
subgraph "On-Prem DCs"
AUC[Auckland-DC 🇳🇿]
SYD[Syndey-DC 🇦🇺]
DSAgent[DataSync Agent]
AUC -- LAN --> DSAgent
end
%% ─────────────────────────
%% DIRECT CONNECT connectionS
%% ─────────────────────────
dxcon-megaport[Global Switch SY6<br/>200 Mbps]:::dx
dxcon-aws-equinix[Equinix SY1-4<br/>1 Gbps]:::dx
dxcon-aws-dx-NZ-AUS[DX Auckland<br/>1 Gbps]:::dx
classDef dx fill:#fdf6e3,stroke:#586e75,stroke-width:1px;
%% ─────────────────────────
%% VIRTUAL INTERFACES (VIFs)
%% ─────────────────────────
dxvif-1[VIF 1905 - megaport-aws-transit]:::vif
dxvif-2[VIF 101 - equinix-tgw]:::vif
dxvif-3[VIF 100 - auckland-tgw]:::vif
dxvif-4[VIF 999 - unused-demo]:::vif
classDef vif fill:#eee8d5,stroke:#657b83;
%% Attachments (some purposely wrong / missing)
dxcon-megaport -->|VLAN 1905| dxvif-1
dxcon-aws-equinix -->|VLAN 101 | dxvif-2
dxcon-aws-dx-NZ-AUS -- VLAN 100 --> dxvif-3
%% Missed link on purpose: dxcon-aws-equinix not connected to dxvif-4
%% ─────────────────────────
%% DIRECT CONNECT GATEWAYS
%% ─────────────────────────
DXGW1[tgw-megaport-dx-gateway]
DXGW2[tgw-aws-outbound-security-dx-gateway]
%% Map VIFs to DXGWs (one wrong on purpose)
dxvif-1 --> DXGW1
dxvif-2 --> DXGW1
dxvif-3 --> DXGW1
dxvif-4 -. dashed .-> DXGW2
%% ─────────────────────────
%% TRANSIT GATEWAYS
%% ─────────────────────────
TGWShared[tgw-aws-shared-services<br/>ASN 64600]:::tgw
TGWOutbound[tgw-aws-outbound-security<br/>ASN 64600]:::tgw
classDef tgw fill:#e8f4fa,stroke:#268bd2,stroke-width:1px;
DXGW1 --> TGWShared
DXGW2 --> TGWOutbound
%% ─────────────────────────
%% VPCs / AWS SERVICES
%% ─────────────────────────
VPC1[Shared-Svcs VPC<br/>10.20.0.0/19]
FWVPC[Security / FW VPC<br/>10.24.128.0/20]
S3[S3 Landing Bucket]
TGWShared --> VPC1
TGWOutbound --> FWVPC
TGWShared -. replicate .-> S3
%% ─────────────────────────
%% DATA TRANSFER PATH
%% ─────────────────────────
DSAgent -- DX path --> dxcon-aws-dx-NZ-AUS
DSAgent -. parallel streams .- S3Well-Architected Review¶
| Pillar | Strengths | Gaps |
|---|---|---|
| Network Design | Multiple POPs (Megaport, Equinix, Auckland) gives path diversity; jumbo MTU configured. | No MACsec; single DXGW per TGW ≈ blast radius. |
| Security | TGW segmentation between shared services and egress; prefixes tightly scoped. | Frames traverse L2 unencrypted; flow logs not enabled on TGWs. |
| Reliability | Separate 200 Mbps & 1 Gbps connections; TGW route-domain isolation. | No Bidirectional Forwarding Detection (BFD); failover latency > 3 s. |
Recommendations & Improvements¶
- Enable MACsec or IPsec-over-DX on all connections (Megaport now offers MACsec on MCR v2).
- Deploy BFD with 300 ms intervals on all BGP sessions for sub-second failover.
- Introduce a second TGW per account (e.g.,
tgw-non-prod) to reduce route-table blast radius. - Centralise prefix-list governance in AWS RAM to prevent drift between DXGW attachments.
- Automate DX Health Monitoring with EventBridge alarms on
bgpStateChange, capturingNotificationType = Outage. - Cost-optimise port mix—down-shift Megaport to 100 Mbps for DEV hours; use Port-Speed-Flex feature.
Security Considerations¶
- Encryption Status: Currently down, potentially exposing sensitive data traversing physical connections.
- MACsec Disabled: Lacks layer-2 encryption, increasing vulnerability.
-
Mitigation via Design:
-
Utilize application-level encryption (TLS) for sensitive data.
- Implement VPC endpoint policies and rigorous IAM roles to minimize data exposure risk.
- Continuous monitoring and anomaly detection using AWS Network Firewall, CloudWatch, and CloudTrail.
FinOps & Governance¶
Cost optimization recommendations:
- Implement consistent resource tagging (
CostCenter,Environment,Application) for precise spend tracking. - Regularly audit DX connections to scale bandwidth appropriately and avoid underutilized or over-provisioned links.
- Utilize AWS Cost Explorer for continuous cost visibility and forecasting.
As-Built Diagram (Mermaid)¶
graph TD
dxcon-megaport[Global Switch SY6 200 Mbps] -- VLAN1905 --> dxvif-1 -- attach --> tgw-aws-shared-services
dxcon-aws-equinix[Equinix SY1–SY4 1Gbps] -- VLAN101 --> dxvif-2 -- attach --> tgw-aws-shared-services
dxcon-aws-dx-NZ-AUS[Auckland Data Center 1Gbps] -- VLAN100 --> dxvif-3
%% Intentional errors below
dxvif-3 attach tgw-outbound-security
tgw-aws-shared-services --- Direct-Connect-gateway-3
Direct-Connect-gateway-2 - aws-shared-services
Direct-Connect-gateway-1 -->|Missing Link| tgw-aws-outbound-securityWell-Architected Review¶
Analyzed against AWS Well-Architected Framework:
Network Design¶
- Strengths: Clear isolation via VLANs and TGW segmentation, scalable connectivity.
- Gaps: MACsec and link encryption missing; jumbo frames available but underutilized without end-to-end consistency.
Security¶
- Strengths: Dedicated TGWs and DX gateways enforce traffic segmentation.
- Gaps: "Encryption Down" introduces compliance risks; must leverage additional encryption at higher layers.
Reliability¶
- Strengths: Multiple redundant DX paths (Megaport, Equinix, Auckland) providing failover capability.
- Gaps: Lack of BFD for faster DX failover detection and no automated health-check alarms configured.
Recommendations & Improvements¶
- Enable MACsec: Secure L2 traffic encryption and compliance.
- Activate Encryption Modes: Implement end-to-end encryption (AWS VPN overlay) if MACsec unavailable.
- DX Health Monitoring: Enable AWS CloudWatch and Direct Connect alarms for proactive fault detection.
- Centralize TGW Route Management: Adopt a centralized TGW routing domain to reduce complexity.
- Jumbo Frames Consistency: Ensure end-to-end MTU alignment (set MTU=8500) to optimize throughput.
Implementing these enhancements significantly improves overall architecture security, reliability, and operational efficiency, ensuring robust, scalable hybrid-cloud connectivity suitable for enterprise-grade workloads.
AWS Data Transfer Cost¶
flowchart LR
%%===========================
%% REGIONS & CORE SERVICES
%%===========================
subgraph "AWS Region A"
EC2A["EC2 (AZ-A)"]
RDSA["RDS"]
ALB["ALB"]
NLB["NLB"]
CLB["CLB"]
S3A["S3 / EFS / DynamoDB"]
NAT["Managed NAT\n+$0.045/GB"]
PL["PrivateLink\n$0.004-0.01"]
end
subgraph "AWS Region B"
EC2B["EC2 (AZ-B)"]
RDSB["RDS"]
end
Internet[(Internet)]
CF["CloudFront\n$0.085-0.12"]
GA["Global Accelerator\n$0.015-1.05"]
DX["Direct Connect\n$0.03-0.11"]
TGW["Transit Gateway\n$0.02-0.19"]
%%===========================
%% EDGES WITH COST LABELS
%%===========================
%% Internet paths
Internet -->|Inbound FREE| EC2A
EC2A -->|$0.09-0.05/GB| Internet
%% CloudFront overlay
CF -->|1 TB/mo free| EC2A
EC2A -->|$0.085-0.12| CF -->|to Internet| Internet
%% Global Accelerator
EC2A -->|$0.02-0.16| GA --> EC2B
%% Direct Connect
EC2A -->|$0.03-0.11| DX
%% Region-to-region
EC2A <-->|$0.02/GB<br/>$0.01 us-e1↔e2| EC2B
%% Cross-AZ inside Region A
EC2A <-->|$0.01-0.02| RDSA
EC2A <-->|$0.01-0.02| ALB
EC2A <-->|$0.01-0.02| NLB
%% NAT surcharge
Internet <-->|+$0.045| NAT
%% PrivateLink cheaper option
EC2A --- PL --- S3A
%% Transit Gateway hub-and-spoke
EC2A --> TGW
TGW -->|$0.02-0.19| EC2B